In this lunchtime #WPQuickies, I show you how to keep track of plugins flagged with vulnerabilities so that you can be one step ahead of the hackers.
What Vulnerabilities?
There are a heap of ways a plugin (or theme) can become vulnerable to attack:
- SQL Injection – where the bad actor tries to enter SQL statements into form fields or URL parameters. This mostly happens because the plugin author is not properly sanitising user input.
- Cross-Site-Scripting – similar to SQL Injection – the bad actor tries to save code into the database through comments or other input fields to steal the cookie or PHP session information of your logged-in admin user.
- Malware – already infected plugins from untrustworthy sites (torrents etc.).
- Nulled Plugins – Some plugins and themes can cost a lot, so people will try to find them for free or with their license “nulled” – that’s a big mistake! This is more common than you may think.
- Old Libraries – as plugins become more complex, they tend to rely on external libraries. If any of these libraries have not patched vulnerabilities, it’s another vector for bad actors to compromise your site with.
- Compromised Uploads – always be wary of plugins that allow users to upload files. There’s a huge opportunity for bad actors to upload code files and run them on the webserver.
- Privilege Escalation – when a bad actor uses a low-level user login subscriber/contributor and a vulnerability in assigning user roles and capabilities to perform actions that the user should not perform (install plugin/add new user etc.)
Update WordPress Frequently
Of course, you can avoid most of these issues simply by updating your WordPress core, plugins and themes frequently.
Frequently is a relative term – so how often should you be updating your WordPress site?
At least weekly – definitely immediately if you are aware of a vulnerability.
Always test your updates on a staging server to see if there are any issues before applying the same sequence of updates to your live production website.
Where Can You Find Info On Vulnerable Plugins?
There are a few sources that you can use to get ahead of the curve and find out vulnerabilities in WordPress core, plugins and themes.
WPScan
This is probably your best source for all WordPress vulnerabilities and is used by a lot of WordPress-related SaaS services.
You can view vulnerabilities by core, plugins and themes at https://wpscan.com/.
There is also an API (free and paid) if you are a developer and want to write your own code to check your own or client’s websites.
WPScan also have an official WordPress plugin which will email you should it find an issues with your site.
WPScan – WordPress Security Scanner
Wordfence Blog and Plugin
Wordfence has a blog category dedicated to WordPress vulnerabilities at https://www.wordfence.com/blog/category/vulnerabilities/.
They also have a fantastic security plugin which will notify you of any security issues with core, plugin and themes.
Wordfence Security – Firewall & Malware Scan
I use Wordfence on all my personal and client sites.
There is a free version of the plugin which does daily scans or a premium version which gets real-time threat updates.
Sucuri Blog and Plugin
The Sucuri blog has a section dedicated to WordPress Security covering more than just the WordPress core, plugin and theme vulnerabilities https://blog.sucuri.net/?fwp_blog_categories=wordpress-security
Sucuri also have a plugin at which will scan your site and email you with vulnerability issues.
Sucuri Security – Auditing, Malware Scanner and Security Hardening
ManageWP SaaS
Using a SaaS service such as ManageWP allows you to instantly see any plugin vulnerabilities across all your sites.
There is a warning icon on the dashboard that tells you one or more vulnerability has been detected.
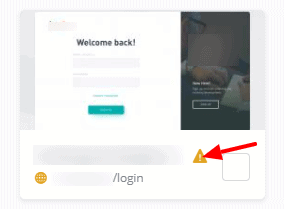
The website dashboard view indicates which plugin, themes or core versions have a detected vulnerability and needs an immediate patch.
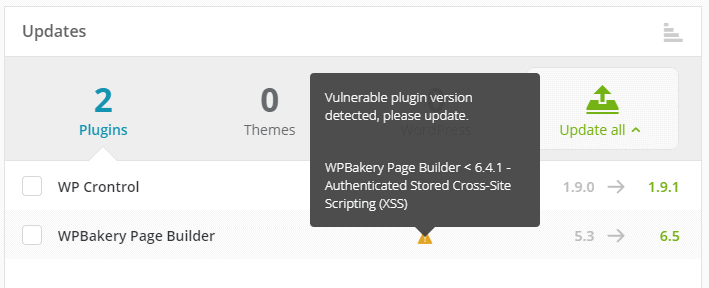
If you manage a client websites support and maintenance – sometimes they will let a license expire and you can’t apply updates.
If this happens you need to get written consent from them that if their site is hacked due to vulnerabilities in licence-expired plugins or themes, that you are not held responsible.
I have similar wording in my WP Wingman WordPress site care plan T&C’s.
Conclusion
There you have it.
That’s my round-up of where to go to track WordPress vulnerabilities for core, plugins and themes.
I hope you found the information useful.
It may be worthwhile checking your own and client sites for any issues today.
#WPQuickies
Join me every Thursday at 1 pm Sydney time for some more WPQuickies – WordPress tips and tricks in thirty minutes or less.
Broadcasting live on YouTube and Facebook.
Suggest a #WPQuickies Topic
If you have an WordPress topic you’d like to see explained in 30 mins or under, fill out the form below.
https://forms.gle/mMWCNd3L2cyDFBA57